Sensor Development Software for IoT Devices
Throughout the last decade, the research area of wirelessly networked sensors has been one of the most popular among computer engineers and scientists. With recent initiatives such as Cyber-Physical Systems, Internet of Things, and Planetary Skin, sensor-based applications have gained new momentum in the research community and industry beyond the realm of computer engineers and scientists. Therefore, today wireless sensors are not only used by computer engineers and scientists, but also by ecologists for observing wildlife, geophysicists for monitoring seismic activities of volcanoes, farmers for precision agriculture, civil engineers for monitoring the health of deteriorating civil structures like highways and bridges, medical doctors and nurses for monitoring patients, and technology enthusiasts to develop applications.
Currently this diverse group of engineers and scientists have two options: expend considerable expense on proprietary data acquisition systems, or expend considerable time on learning the development and engineering skills necessary to create their own solutions from more affordable off the shelf components. Neither of these solutions is truly optimal and thus hamper the development and data collection experience. To minimize the complexity and reduce the cost of implementing these sensor networks, a new extensible, scalable, cross-platform, and open-source wireless sensor software development framework called PROVIZ is proposed in this project.
Need For Sensor Development Framework
There are many scenarios in which engineers and scientists may need to acquire data from a system or environment using a network of sensors. These sensors are tools and a means to the end of acquiring relevant data. A minimum of time and effort should be dedicated to configuring and maintaining them. Using and configuring these sensor networks should not require any special knowledge from the user, it should be a simple tool. Current options require either software development expertise or incur large costs for specialized proprietary systems. The proviz project attempts to remove the barriers of entry into the growing IoT world so engineers and scientist have the tools they need to continue to push innovation and science.
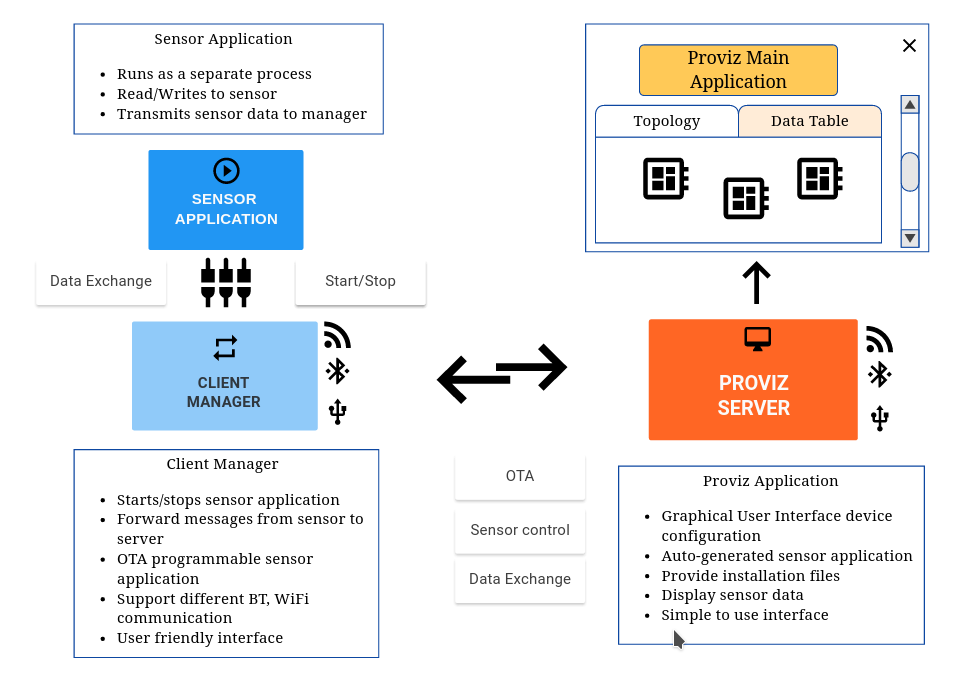
Proviz Topology Overview
Proviz consist of four main components,
- The Proviz Main Application and User Interface
- The Proviz Server
- The Client Mananger
- The Sensor Application
Figure 1: Proviz Topology Overview
Proviz Main Application
[BURAK]
Proviz Client Application
The Proviz client application is designed to be easily installed and take care all all steps need to get a device up and running as quickly as possible. The client application will control the separate sensor application starting, stopping and replacing the as need. All communication between sensors and device will be relayed back to the Proviz server for the user.
On the Arduino platform the client application takes the form of a C/C++ library. When the user auto-generates the sensor code the library is included and is used in the same regard, controlling the sensor application and relaying data.
Supported Platforms:
|
|
The utilization of sensors in industry and military settings has been around for a long time. Today, myriads of companies offer sensor-based solutions, and the usage of billions of networked sensors are envisioned to be deployed on land, in sea, air, and space to detect and predict the environmental changes in an effort to build a globally pervasive nervous system. Given their low cost and multiple functionalities, they have been predicted to be one of the ten technologies that will change the world in the next 10 years. Moreover, with recent initiatives such as Cyber-Physical Systems, Internet of Things, and Planetary Skin, sensor-based applications have gained new momentum in the research community and industry.
Accordingly, throughout the last decade, the research area of wirelessly networked sensors has been one of the most favorite among computer engineers and scientists. Similarly, the use of wireless sensors has also started to gain popularity among researchers other than computer engineers and scientists. For instance, today sensors are used to enable civil engineers monitor the structural health of deteriorating infrastructure such as highways and bridges (Figure 1), farmers to develop precision-agriculture techniques, ecologists to observe wildlife in their natural habitat, and geophysicists to capture seismic activity of volcanoes.
Fig.1: An example wireless sensor structural health monitoring system deployed by civil engineers [1].
Hence, the wireless sensor researchers’ community comprises of advanced sensor application and protocol developers and scientists/engineers who use wireless sensor networks (WSNs) for simple data gathering. However, the task of developing software applications for wireless sensors is challenging for researchers because sensors have limited technical capabilities and software implementations for sensors require meticulous procedures and extra operations to provide a desired level of services (e.g., reliability, security) for applications. This situation is even further exacerbated for researchers in other fields of engineering and science (e.g., civil engineers and geophysicists) as they may not have a rigorous programming background.
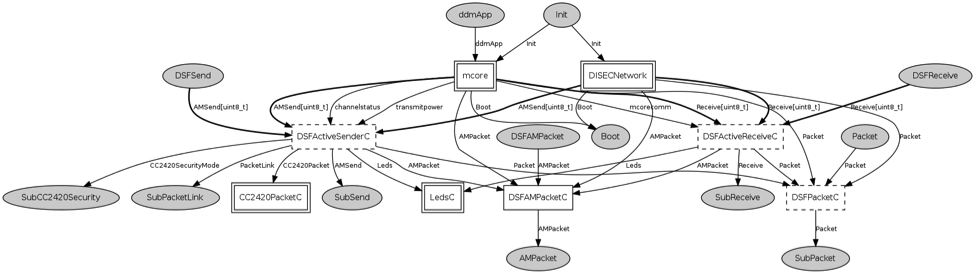
Moreover, engineering and science researchers working with wireless sensors utilize different software tools to achieve the goals of their research activities. For instance, in order to develop, test, visualize, and monitor a WSN application, a developer may need a programming tool, a simulator, and a visualization tool. However, for engineers, scientists, and researchers of other fields (e.g., civil engineer, geophysicist) whose primary goal is to utilize a wireless sensor as an intermediary tool to accomplish the specific tasks of their domains (e.g., collect structural health data from bridges), using a multitude of tools may pose confusion and hamper an efficient scientific experiment opportunity with wireless sensors. An example internal view of wired components and their interactions with each other for a sensor program using TinyOS [2] and nesC [3] is given in Figure 2.
Fig. 2: Internal view of an example wireless sensor program using nesC
As can be seen by the visual complexity of Figure 2, programming wireless sensors is not a trivial task; it requires a sophisticated understanding of the inner architecture of the software environment. In fact, for researchers in other fields of engineering and science (e.g., civil engineers and geophysicists), the task is even further complicated as they may not have a rigorous programming background.
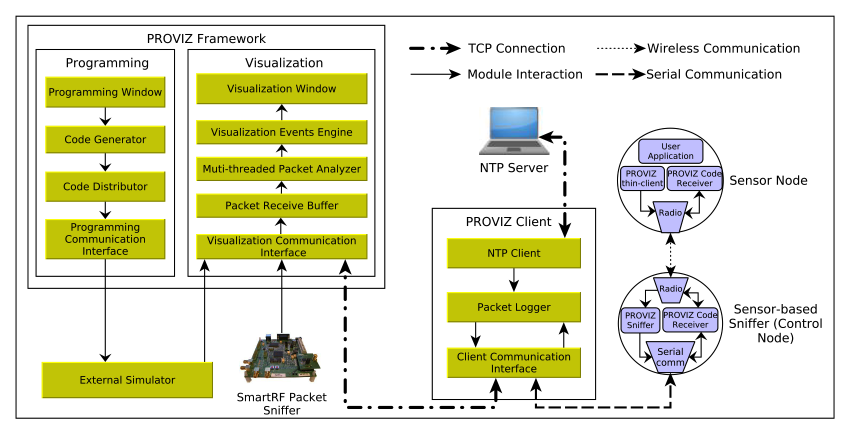
Therefore, to facilitate the design, development and implementation of wireless sensor applications, in this project, we develop a new framework called PROVIZ, which will provide visualization and programming functionalities into a common platform. Furthermore, PROVIZ can visualize the deployment of wireless sensors by continuously monitoring for their transmissions and can be used by researchers for visual debugging purposes.
PROVIZ is conceptualized as an open-source, platform independent, modular, and extensible framework with heterogeneous wireless sensors in mind. Hence, it will be able to work with various sensor types (e.g., MicaZ, Iris, TelosB) and their diverse traffic in real-time. It will provide a set of easy-to-use simplified languages (one domain specific scripting language, one icon-based drag-and-drop style visual language) and a simple programming editor for developing wireless sensor applications and a mechanism for (re)programming wireless sensor nodes remotely over-the-air by distributing the generated application image. In this way with PROVIZ, wireless software development process can be expedited and simplified. PROVIZ will have the capability to visualize wireless sensor data captured either from a packet sniffer (a live sensor-based sniffer or from a binary packet trace file (PSD format) generated by a commercial sniffer (e.g., TI SmartRF packet sniffer)) or from an external simulator (e.g., OMNeT) running a wireless sensor application. Also, PROVIZ will be able to work with multiple sniffers simultaneously in a distributed setup to visualize a large wireless sensor deployment. Finally, PROVIZ will include a built-in capability to demonstrate different sensor deployments, which will allow the science and engineering researchers to quickly craft various application scenarios and share them with their peers. An overview of PROVIZ’s design is illustrated in Figure 3. The PROVIZ framework will provide two fundamental functionalities to researchers. One is the ability to visualize the sensor data collected in real a network or generated in an external simulator while the other is the ability to easily program sensor nodes.
References
[1]. Georgia Tech Laboratory for Smart Structural Systems, Development of Wireless Structural Sensing and Control Devices, http://wang.ce.gatech.edu/research.htm.
[2] TinyOS homepage, http://www.tinyos.net.
[3] nesC: A Programming Language for Deeply Networked Systems, http://nescc.sourceforge.net.
You can reach Proviz source code by filling source code release request form.
- Refereed Journal and Magazine Articles
- Refereed Book Chapters
- Refereed Conference Papers
- Refereed Demos and Posters
- Media Coverage
Refereed Journal and Magazine Articles:
- Hidayet Aksu, A. Selcuk Uluagac, and Elizabeth S. Bentley, “Identification of Wearable Devices with Bluetooth,” Accepted to Appear in IEEE Transactions on Sustainable Computing, February 2018
- Gabriele Tolomei, Leo Babun, Hidayet Aksu, A. Selcuk Uluagac, and Mauro Conti “ Advertising in the IoT Era: Vision and Challenges,” Accepted to Appear in IEEE Communications Magazine, January 2018
- S. Tonyali, K. Akkaya, N. Saputro, A. S. Uluagac, and M. Nojoumian, “privacy-preserving protocols for secure and reliable data aggregation in iot-enabled smart metering systems,” Elsevier Future Generation Computer Systems Journal, Volume 78, Part 2, Pages 547-557, January 2018, pdf
- Juan Lopez, Leonardo Babun, Hidayet Aksu, and A. Selcuk Uluagac, “A Survey on Function and System Call Hooking Approaches,” Springer Journal of Hardware and Systems Security, Volume 1, Issue 2, pp 114-136, June 2017, pdf
- H. Menouar, I. Guvenc, K. Akkaya, A. S. Uluagac, A. Kadri, and A. Tuncer, “Uav-enabled intelligent transportation systems for the smart city: Applications and challenges,” IEEE Communications Magazine, vol. 55, no. 3, pp. 22–28, March 2017, pdf
- Mehmet Cintoglu, Kemal Akkaya, Osama Mohammed, and A. Selcuk Uluagac, “A Survey on Smart Grid Cyber-Physical System Testbeds,” IEEE Communications Surveys and Tutorials, vol.PP, no.99, pp.1-1, Nov 3, 2016, [bibtex],[pdf]
- Shruthi Ravichandran, Ramalingam K. Chandrasekar, A. Selcuk Uluagac, and R. A. Beyah,”A Simple Visualization and Programming Framework for Wireless Sensor Networks: PROVIZ,” Elsevier Ad Hoc Networks Journal, Volume 53, 15 December 2016, Pages 1-16, ISSN 1570-870, [bibtex],[pdf]
- Gong Chen, Jacob H. Cox Jr, A. Selcuk Uluagac, and John A. Copeland, “In-depth Survey of Digital Advertising Technologies,” IEEE Communications Surveys and Tutorials, vol. 18, no. 3, pp. 2124-2148, 25 January 2016, [bibtex],[pdf]
- Sakthi V. Radhakrishnan, A. Selcuk Uluagac, and Raheem A. Beyah,”GTID: A Technique for Physical Device and Device Type Fingerprinting,” Transactions on Dependable and Secure Computing (TDSC), vol. 12, no 5, pp: 519-532, Sept.-Oct. 2015, [bibtex],[pdf]
- Shouling Ji, Jing He, A. Selcuk Uluagac, Raheem Beyah, and Yingshu Li. “Cell-based Snapshot and Continuous Data Collection in Wireless Sensor Networks.” ACM Transactions on Sensor Networks, vol. 9, no 4, pp: 47:1-47:29, Jul. 2013, [bibtex], [pdf]
- A. Selcuk Uluagac, R. A. Beyah, and J. A. Copeland, “Secure Source-Based Loose Synchronization (SOBAS) for Wireless Sensor Networks”, IEEE Transactions on Parallel and Distributed Systems, vol. 24, no. 4, pp. 803-813, April 2013, [bibtex], [pdf]
- Shouling Ji, A. Selcuk Uluagac, R. Beyah, and Z. Cai. “Virtual Backbone based Unicasting and Convergecasting in Cognitive Radio Networks”, Springer Journal of Combinatorial Optimization, January 2012, [bibtex], [pdf]
- C. P. Lee, A. Selcuk Uluagac, K.Fairbanks, and J. A. Copeland, ”The Design of NetSecLab: A Small Competition-Based Network Security Lab”, IEEE Transactions on Education, Vol 54, Issue 1, March 2011, [bibtex], [pdf]
- A. Selcuk Uluagac, Raheem A. Beyah, Yingshu Li, John A. Copeland, “VEBEK: Virtual Energy-Based Encryption and Keying for Wireless Sensor Networks,” IEEE Transactions on Mobile Computing, vol. 9, no. 7, pp. 994-1007, July 2010, [bibtex],[pdf]
Refereed Book Chapters:
- A. Selcuk Uluagac, Kemal Akkaya, Apurva Mohan, Hazar Cintuglu, Tarek Youssef, Osama Mohammed, “Wireless Communication in ICSs,” Book Chapter in Cyber Security Methods for Industrial Control and SCADA Systems, Edited by Ed Colbert and Alex Kott, Springer, vol: 66, Pages 29-49, September 2016, ISBN 978-3-319-32125-7, pdf
- Nico Saputro, Ali Yurekli, Kemal Akkaya, and A. Selcuk Uluagac, “Privacy-preservation for IoT in Smart Buildings,” Book Chapter in Security and Privacy in Internet of Things (IoT): Models, Algorithms, and Implementations, edited by Fie Hu, Pages 135–166, April 1, 2016, CRC Press, ISBN 9781498723183, pdf
- Kemal Akkaya, A. Selcuk Uluagac, Abdullah Aydeger, and Apurva Mohan, “Secure Software Defined Networking Architectures for The Smart Grid,” Book Chapter in Smart Grid: Networking, Data Management and Business Models, edited by Hussein Mouftah and Melike Erol Kantarci, Pages 53–70, April 1, 2016, CRC Press, ISBN 9781498719704, pdf
Refereed Conference Papers:
- Cengiz Kaygusuz, Leonardo Babun, Hidayet Aksu and Selcuk Uluagac, “Detection of Compromised
Smart Grid Devices with Machine Learning and Convolution Techniques,” in Proc. of the IEEE
International Conference on Communications (ICC), May 2018, Kansas City, MO, USA - Abbas Acar, Hidayet Aksu, Kemal Akkaya, and A. Selcuk Uluagac, “WACA: Wearable-Assisted Continuous Authentication,” 3rd International Workshop on Bio-inspired Security, Trust, Assurance and Resilience co-located with 39th IEEE Symposium on Security and Privacy (IEEE S&P 2018), Oakland, CA, May 24, 2018.
- Amit Kumar Sikder, Hidayet Aksu, A. Selcuk Uluagac, and Mauro Conti, “IoT-enabled Smart Lighting Systems for Smart Cities,” in Proc. of the 8th IEEE Computing and Communication Workshop and Conference (CCWC), Las Vegas, NV, USA, January 2018
- Abdullah Aydeger, Nico Saputro, Kemal Akkaya, and Selcuk Uluagac, “Assessing the Overhead of Authentication during SDN-Enabled Restoration of Smart Grid Inter-substation Communications,” in Proc. of the IEEE Consumer Communications & Networking Conference (CCNC) Conference, Las Vegas, NV, January 2018.
- A. K. Sikder, H. Aksu, and A. S. Uluagac, “6thsense: A context-aware sensor-based attack detector for smart devices,” in Proc. of the 26th USENIX Security Symposium, Vancouver, BC, 2017, pdf
- A. Acar, Z. B. Celik, H. Aksu, A. S. Uluagac, and P. McDaniel, “Achieving secure and differentially private computations in multiparty settings,” in Proceedings of the IEEE Symposium on Privacy-Aware Computing (IEEE PAC). D.C., USA: IEEE, 2017
- A. Akkiraju, D. Gabay, B. Yesilyurt, H. Aksu, and A. S. Uluagac, “Cybergrenade: Automated exploitation of local network machines via single board computers,” in Proc. of the 4th National Workshop for REU Research in Networking and Systems, Orlando, FL, USA, 2017
- Leonardo Babun, Hidayet Aksu, and A. Selcuk Uluagac, “Identifying Counterfeit Smart Grid Devices: A Lightweight System Level Framework,” in Proc. of the IEEE International Conference on Communications (ICC), France, May 2017
- Edwin Vattapparamban, Ismail Guvenc, Ali Ihsan Yurekli, Kemal Akkaya, and A. Selcuk Uluagac, “Drones for Smart Cities: Issues in Cybersecurity, Privacy, and Public Safety,” in Proc. of the IEEE International Wireless Communications & Mobile Computing Conference (IWCMC) Smart Cities and Smart Mobility Platforms Symposium, Paphos, Cyprus, September 2016.
- Abdullah Aydeger, Mehmet Cintoglu, Kemal Akkaya, Osama Muhammed, and A. Selcuk Uluagac, “Software Defined Networking for Resilient Communications in Smart Grid Active Distribution Networks,” in Proc. of the IEEE International Conference on Communications (ICC), Malaysia, May 2016
- Kyle Denney, A. Selcuk Uluagac, and Kemal Akkaya, “A Novel Storage Covert Channel on Wearable Devices Using Status Bar Notifications”, in Proceedings of the IEEE Consumer Communications & Networking Conference (CCNC) Conference, Las Vegas, NV, January 2016
- Samet Tonyali, Kemal Akkaya, Nico Saputro, A. Selcuk Uluagac, “A Reliable Data Aggregation Mechanism with Homomorphic Encryption in Smart Grid AMI Networks”, in Proceedings of the IEEE Consumer Communications & Networking Conference (CCNC) Conference, Las Vegas, NV, January 2016
- Chris Wampler, A. Selcuk Uluagac, and Raheem Beyah ”Information Leakage in Encrypted IP Video Traffic,” In Proceedings of the IEEE Global Communications (GLOBECOM) Conference, San Diego, CA, USA, December 2015
- Troy Nunnally, A. Selcuk Uluagac, and R. A. Beyah, “InterSec: An Interaction System for Network Security Applications,” in Proceedings of the IEEE International Conference on Communications (ICC), London, UK, June 2015
- Jinyoun Cho, A. Selcuk Uluagac, J. A. Copeland, and Yusun Chang ”Efficient Safety Message Forwarding using Multi-Channels in Low Density VANETs,” In Proceedings of the IEEE Global Communications (GLOBECOM) Conference, Austin, TX, December 2014
- A. Selcuk Uluagac, Venkatachalam S., and Raheem A. Beyah,”Sensory Channel Threats to Cyber Physical Systems: A Wake-up Call,” In Proceedings of the IEEE Conference on Communications and Network Security (CNS), October 2014, San Francisco, USA
- Aaron Goldman, A. Selcuk Uluagac, and J. A. Copeland, ”Cryptographically-Curated File System (CCFS): Secure, Inter-operable, and Easily Implementable Information-Centric Networking,” In Proceedings of the IEEE International Conference on Local Computer Networks (LCN), September 2014, Edmonton, Canada
- Xiaojing Liao, A.Selcuk Uluagac, and R. A. Beyah, “S-MATCH: Verifiable Privacy-preserving Profile Matching for Mobile Social Services,”in Proceedings of the 44th Annual IEEE/IFIP International Conference on Dependable Systems and Networks (DSN 2014), June 2014, Atlanta, USA
- Wenyi Liu, A. Selcuk Uluagac, and Raheem Beyah, “MACA: A Privacy-Preserving Multi-factor Cloud Authentication System Utilizing Big Data”, in Proceedings of the IEEE INFOCOM Workshop on Security and Privacy in Big Data, April 2014, Toronto, Canada
- Albert Brzeczko, A. Selcuk Uluagac, Raheem Beyah, and John A. Copeland, “Active Deception Model for Securing Cloud Infrastructure”, in Proceedings of the IEEE INFOCOM Workshop on Security and Privacy in Big Data, April 2014, Toronto, Canada
- A. Selcuk Uluagac, Sakthi V. Radhakrishnan, Cherita Corbett, Antony Baca, and Raheem A. Beyah,”A Passive Technique for Fingerprinting Wireless Devices with Wired-side Observations,” in Proceedings of the IEEE Conference on Communications and Network Security (CNS), October 2013, [bibtex],[pdf]
- Sakthi V. Radhakrishnan, A.Selcuk Uluagac, and R. A. Beyah,”Realizing an 802.11-based Covert Timing Channel using Off-The-Shelf Wireless Cards,” in Proceedings of the IEEE Global Communications (GLOBECOM) Conference, Atlanta, GA, December 2013, [bibtex],[pdf]
- Troy Nunnally, Kulsoom Abdullah, A. Selcuk Uluagac, J. A. Copeland, and R. A. Beyah, “NAVSEC : A Recommender System for 3D Network Security Visualizations”, in Proceedings of the ACM Visualization for Cyber Security Workshop (VizSec), October 2013, [bibtex],[pdf]
- Ramalingam K. C., A.Selcuk Uluagac, and R. A. Beyah,“PROVIZ: An Integrated Visualization and Programming Framework for WSNs,“ in Proceedings of the 8th IEEE Workshop on Practical Issues in Building Sensor Network Applications 2013 (IEEE SenseApp 2013), Australia, October 2013, [bibtex],[pdf]
- Venkatachalam S., A. Selcuk Uluagac, and Raheem Beyah, “Examining the Characteristics and Implications of Sensor Side Channels“, in Proceedings of the IEEE International Conference on Communications (ICC), Budapest, Hungary, June 2013,[bibtex],[pdf]
- Troy Nunnally, Penyen Chi, Kulsoom Abdullah, A. Selcuk Uluagac, and R. A. Beyah, “P3D: A Parallel 3D Coordinate System for Advanced Network Scans“, in Proceedings of the IEEE International Conference on Communications (ICC), Budapest, Hungary, June 2013,[bibtex],[pdf]
- Marco Valero, A. Selcuk Uluagac, Venkatachalam S., Ramalingam K. C., and Raheem Beyah, “The Monitoring Core (M-Core): A Modular Architecture for Rapid Sensor App Development“, in Proceedings of the IEEE International Conference on Mobile Ad-hoc and Sensor Systems (MASS), October 2012, [bibtex],[pdf]
- Aaron Goldman, A. Selcuk Uluagac, R. A. Beyah, and J. A. Copeland, ”Plugging the Leaks without Unplugging your Network in the Midst of Disaster,” in Proceedings of the IEEE International Conference on Local Computer Networks (LCN), October 2012, [bibtex],[pdf]
- Troy Nunnally, A. Selcuk Uluagac, R. A. Beyah, and J. A. Copeland, “3DSVAT: A 3D Stereoscopic Vulnerability Assessment Tool for Network Security”, in Proceedings of the IEEE International Conference on Local Computer Networks (LCN), October 2012, [bibtex],[pdf]
- Ramalingam K. C., Venkatachalam Subramanian, A.Selcuk Uluagac, and R. A. Beyah,“Secure Distribution of Images for Wireless Sensor Networks,“ in Proceedings of the IEEE Global Communications (GLOBECOM) Conference, Anaheim, CA, December 2012, [bibtex],[pdf]
- Marco Valero, Sang Shin Jung, A. Selcuk Uluagac, Yingshu Li, Raheem Beyah, “Di-Sec: A Distributed Security Framework for Heterogeneous Wireless Sensor Networks“, in Proceedings of the IEEE INFOCOM Conference, Orlando, FL, March 2012, [bibtex],[pdf]
- A. Selcuk Uluagac, R. A. Beyah, and J. A. Copeland, “TIme-Based DynamiC Keying and En-Route Filtering (TICK) for Wireless Sensor Networks,“ in Proceedings of the IEEE Global Communications (GLOBECOM) Conference, Miami, FL, December 2010, [bibtex],[pdf]
- A.Selcuk Uluagac, Roma Kane, Siddharth Joshi, R. A. Beyah, and J. A. Copeland, “Analysis of Varying AS Path Lengths from the Edge of the Network,“ in Proceedings of the IEEE International Communications Conference (ICC), Cape Town, South Africa, May 2010, [bibtex],[pdf]
- A. Selcuk Uluagac, T. Fallon, W. Thain, and J. A. Copeland, ”Development of Undergraduate Network Security Labs with Open Source Tools,” in Proceedings of the American Society for Engineering Education (ASEE) Annual Conference of Composition and Exhibition, Austin, TX, June 2009, [bibtex], [pdf]
- A. Selcuk Uluagac, C. P. Lee, R. A. Beyah, and J. A. Copeland, “Designing Secure Protocols for Wireless Sensor Networks,“ in Proceedings of the 3rd International Conference on Wireless Algorithms, Systems and Applications (WASA), Dallas, Texas, October 2008 (also available in Lecture Notes in Computer Science (LNCS) 5258, Springer-Verlag, pp. 503-514, 2008), [bibtex],[pdf]
- A. Selcuk Uluagac and D. Williams, “Building Hardware-based Low-Cost Experimental DSP Learning Modules,“ in Proceedings of the American Society for Engineering Education (ASEE) Annual Conference of Composition and Exhibition, Pittsburgh, PA, June 2008, [bibtex], [pdf]
- R. Butera, M. Clark, A. Deck, M. Torba, S. Trahan, Selcuk Uluagac, D. Williams, “Cooperative University/Industry Development of a Freshman Introduction to ECE Design Course,“ in Proceedings of the American Society for Engineering Education (ASEE) Annual Conference of Composition and Exhibition, Honolulu, Hawaii, June 2007, [bibtex], [pdf]
- A. Selcuk Uluagac and J. M. Peha, “IP Multicast over Cable TV Networks,“ in Proceedings of 5th International Workshop on Networked Group Communications (NGC), Munich, Germany, September 2003 (also available in Lecture Notes in Computer Science 2816, Springer-Verlag, pp. 168-180, 2003), [bibtex],[pdf]
Refereed Demos and Posters:
- Mumin Cebe, Enes Erdin, Kemal Akkaya, Hidayet Aksu and A.Selcuk Uluagac,”Building a Private Bitcoin-based Payment Network among Electric Vehicles and Charging Stations,” Poster at the Annual Research Conference at the University of Florida’s Florida Institute of Cybersecurity Research, Gainesville, FL, March 1, 2018 (Best Poster Award)
- Leonardo Babun, Z. Berkay Celik, Amit K. Sikder, Hidayet Aksu, Gang Tan, Patrick McDaniel, and A. Selcuk Uluagac, “SaINT: Sensitive Information Tracking for IoT Apps,” Demo at the Annual Research Conference at the University of Florida’s Florida Institute of Cybersecurity Research, Gainesville, FL, March 1, 2018 (Best Demo Award)
- Abbas Acar, Hidayet Aksu, Kemal Akkaya, and A. Selcuk Uluagac, “Wearable-assisted Continuous Authentication,” Poster at the Annual Research Conference at the University of Florida’s Florida Institute of Cybersecurity Research, Gainesville, FL, March 1, 2018
- Leonardo Babun, Hidayet Aksu, and A. Selcuk Uluagac, “A Framework for
Counterfeit Smart Grid Device Detection,” Demo at the Annual Research Conference at the University of Florida’s Florida Institute of Cybersecurity Research, Gainesville, FL, March 8, 2017 (Best Demo Award) - Leonardo Babun, Hidayet Aksu, and A. Selcuk Uluagac, “A Framework for Counterfeit Smart Grid
Device Detection,” Poster and Demo at the Annual Department of Energy’s SEEDS Center Research
Meeting, Miami, FL, 19 January 2017 (Best Poster and Demo Award) - Abbas Acar, Hidayet Aksu, Kemal Akkaya, and A.Selcuk Uluagac, ”WACA: Wearable-Assisted Continuous Authentication Framework with Motion Sensors,“ Poster at The 25th USENIX Security Symposium, August 2016
- Abdullah Aydeger, Kemal Akkaya, A. Selcuk Uluagac, “SDN-based Resilience for Smart Grid Communications,” Demo at the IEEE International Conference on Network Function Virtualization and Software Defined Networks, San Francisco, CA, November 2015
- Kyle Denney, A. Selcuk Uluagac, Kemal Akkaya, and Nico Saputro, “A Novel Storage Covert Channel on Wearable Devices Using Status Bar Notifications”, Demo at the IEEE International Conference on Local Computer Networks (LCN), Clearwater Beach, FL, October 2015
- A. Selcuk Uluagac,Wenyi Liu, and Raheem Beyah, “A Multi-factor Re-authentication Framework with User Privacy,” Poster at the IEEE Conference on Communications and Network Security (CNS), San Fransisco, CA, October 2014
- Aaron Goldman, A. Selcuk Uluagac, and J. A. Copeland, ”Cryptographically-Curated File System (CCFS): Secure, Inter-operable, and Easily Implementable Information-Centric Networking,” Demo at the IEEE International Conference on Local Computer Networks (LCN), September 2014, Edmonton, Canada
- Xiaojing Liao, A.Selcuk Uluagac, and R. A. Beyah,“S-Match: An Efficient Privacy-preserving Profile Matching Scheme” Poster at the IEEE Conference on Communications and Network Security (CNS), October 2013.
- Sakthi V Radhakrishnan, A.Selcuk Uluagac, and R. A. Beyah,”A DCF-Based Covert Timing Channel for IEEE 802.11 With Off-The-Shelf Wireless Cards,“ Poster at The 21st USENIX Security Symposium, August 2012
- Marco Valero, Sang Shin Jung, A. Selcuk Uluagac, Yingshu Li, Raheem Beyah, “The Monitoring Core (M-Core): Toward Fully Securing Heterogeneous Wireless Sensor Networks“, Poster at The 27th Annual Computer Security Applications Conference (ACSAC), December 2011
- Marco Valero, Sang Shin Jung, A. Selcuk Uluagac, Yingshu Li, Raheem Beyah, “Di-Sec: A Distributed Security Framework for Heterogeneous Wireless Sensor Networks“, Demo at ACM International Conference on Mobile Computing and Networking (MobiCom), September 2011
Other Unrefereed Articles, Demos, and Posters
- “The Design of NetSecLab: A Small Competition-Based Network Security Lab”, Poster at at The 2010 Georgia Tech Security Summit: Emerging Cyber Security Threats, Georgia Tech Information Security Center (GTISC), October 2010
- “TIme-Based DynamiC Keying and En-Route Filtering (TICK) for Sensor-Based Ceyber-Physical Systems“, Poster at at The 2010 Georgia Tech Security Summit: Emerging Cyber Security Threats, Georgia Tech Information Security Center (GTISC), October 2010
Media Coverage:
- News Article, “FIU students searching for cybersecurity solutions”, NBC Miami, November 26, 2018, link
- News Article, “FIU inspires future learners,” Miami’s Community Newspapers, February 28, 2018, link
- News Article, “How to stop phone apps from spying on you, Stephen Ornes, January 26, 2018, link
- News Article, “Your phone is like a spy in your pocket,” Science News, Maria Temming, January 23, 2018, link
- TV Interview, “Connect U: FIU offers students specialized training in smart devices,” WSVN
Channel 7, Lorena Estrada, December 29, 2017, Miami, FL, link - News Article, “Experts talk cyber attacks on business, lead live hack,” FIU News, Gisela Valencia, December 21, 2017, link
- TV Interview, “FIU Looks to Future With ’Internet of Things’ Degree,” NBC 6 Miami, Jamie Guirola,
Nov 2, 2017, link - News Article, “CyberCorps pays for students’ education, gives them job opportunities,” FIU News,
Diana Hernandez-Alende , October 10, 2017, link - TV Interview, “Guard your gadgets,” WSVN Channel 7, Leisa Williams, November 11, 2016, Miami,
FL, link - TV Interview, “Dangers of Unsecured Surveillance Cameras,” NBC Miami Channel 6, Laura
Rodriguez, August 18, 2016, link - News Article, “Universities, Utility Research Protecting Nation’s Power Grid From Cyber Attacks,”
Homeland Security Today, Anthony Kimery, Editor-in-Chief, October 13, 2015 - News Article, “FIU Works To Protect Against Power Grid Cyber Attacks,” CBS Miami, Giovanna
Maselli, October 12, 2015
** Project Name: SI2-SSE: A Sustainable Wireless Sensor Software Development Framework for Science and Engineering Researchers.
Project Sponsor: National Science Fondation
Project Duration: 09/01/13-08/31/16