Project Description
- Existing Sensor Management System
- Threat Model
- Assumptions and Features
- 6thSense Framework
- Performance
Existing Sensor Management System
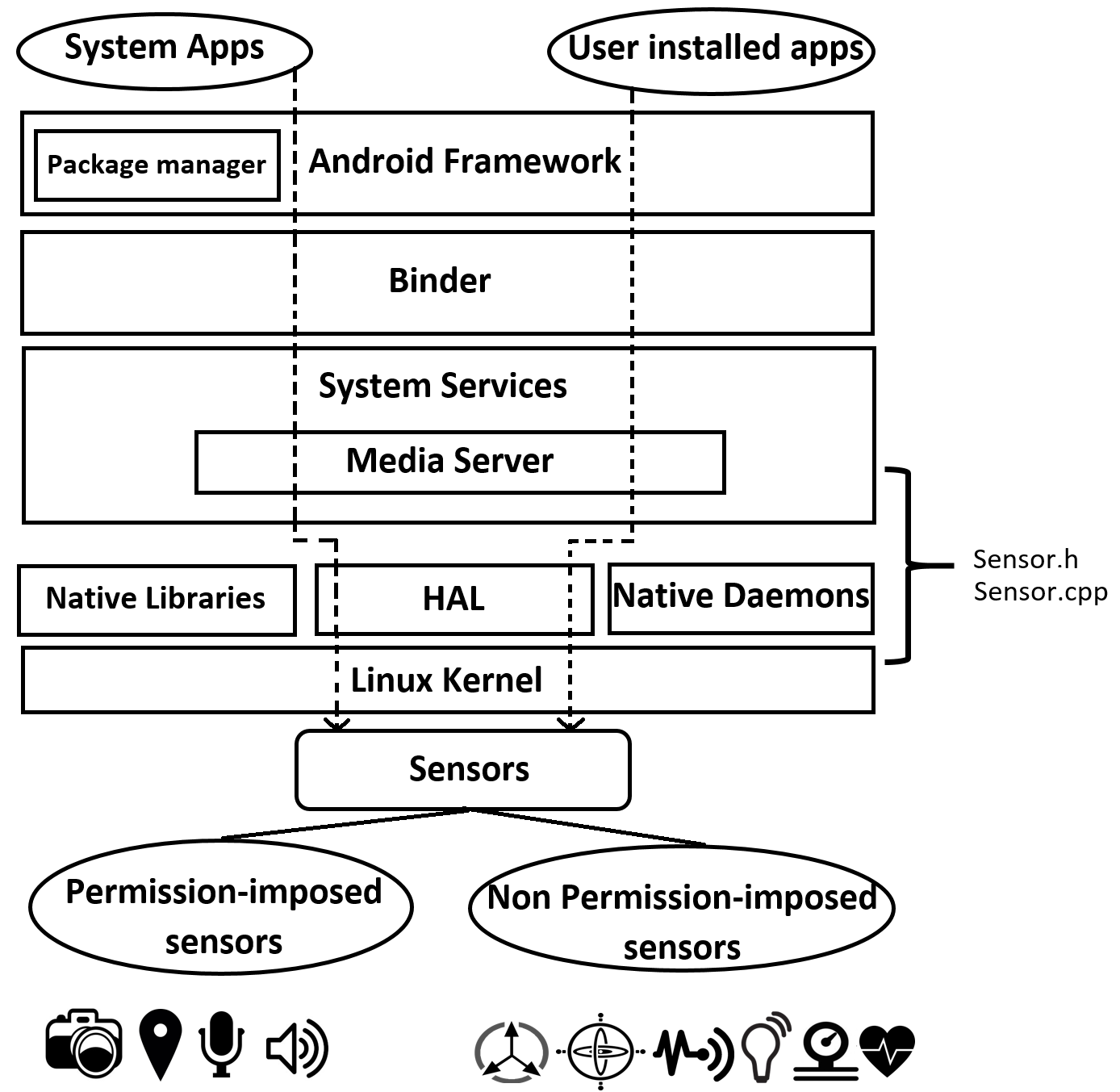
Present smart device operating systems (e.g., Android, Blackberry, iOS, Windows) do not provide any security measure to secure information flow between apps and sensors. Existing sensor management system is built upon permission-based access which is enforced only for selective sensors such as camera, microphone, GPS. Other sensors like gyroscope, light sensor, etc. are considered safe to access by any app. Lack of knowledge about sensor-based threats leads to overlook this design issue. Again, once a user accepts sensor access permission, he/she will have no information regarding how the app is using sensor data in the system. Hence, the existing sensor management system fails to provide complete security to on-board sensors of a smart device.
Figure: Android sensor management system
Threat Model
For testing 6thSense, we classify three different threat models.
Threat 1: Triggering a malicious app via sensor: A malicious app that is already been installed in the device can be triggered by sending a specific pattern via sensors.
Threat 2: Information leakage via sensor: A malicious app existed in the device can leak information (saved or gather in real time) to attackers via sensors.
Threat 3: Stealing information via sensor: A malicious app can exploit camera of a device and capture pictures stealthily when the device is in sleep mode.
Assumptions and Features
For designing 6thSense, we note following design assumptions and features:
Sensor co-dependence: Sensors in smart devices are usually considered as independent components. But for designing 6thSense, we assume that sensors are co-dependent entities. For each user activity on the smart device, a specific set of sensors remains active. For example, if a person is making a call, audio and proximity sensor will remain active. Hence, a co-dependent relation exists between sensors while executing a task. As each activity uses a specific but different set of active sensors to perform the activity, we can distinguish between normal user activity and malicious activities by observing active sensors. 6thSense uses the contexts of all sensors to build the IDS framework and detect malicious activities on the device.
Adaptive sensor sampling: Smart devices come with different sensors which have different ranges of frequencies. To observe and collect sensor data over a specific period, sensor data must be sampled according to sensor frequency correctly. If individual sensor frequency is considered, there may be missing data which will introduce error in the detection method. 6thSense address this issue and sample sensor data over a fixed time period instead of individual sensor frequency.
Faster computation: Smart devices are integrated with the high precision sensors which collect a huge volume of data over a short period for increasing accuracy. To process this data, a faster computation method should be used in proposed security measures. In 6thSense, we use Markov Chain, Naïve Bayes and Machine Learning techniques which are proven simple and faster computation techniques.
Real-time monitoring: A possible way of abusing the sensors is false data injection. If false data is injected, it will introduce error in IDS. To mitigate this issue, 6thSense provide real-time monitoring of sensor data on smart devices.
6thSense Framework
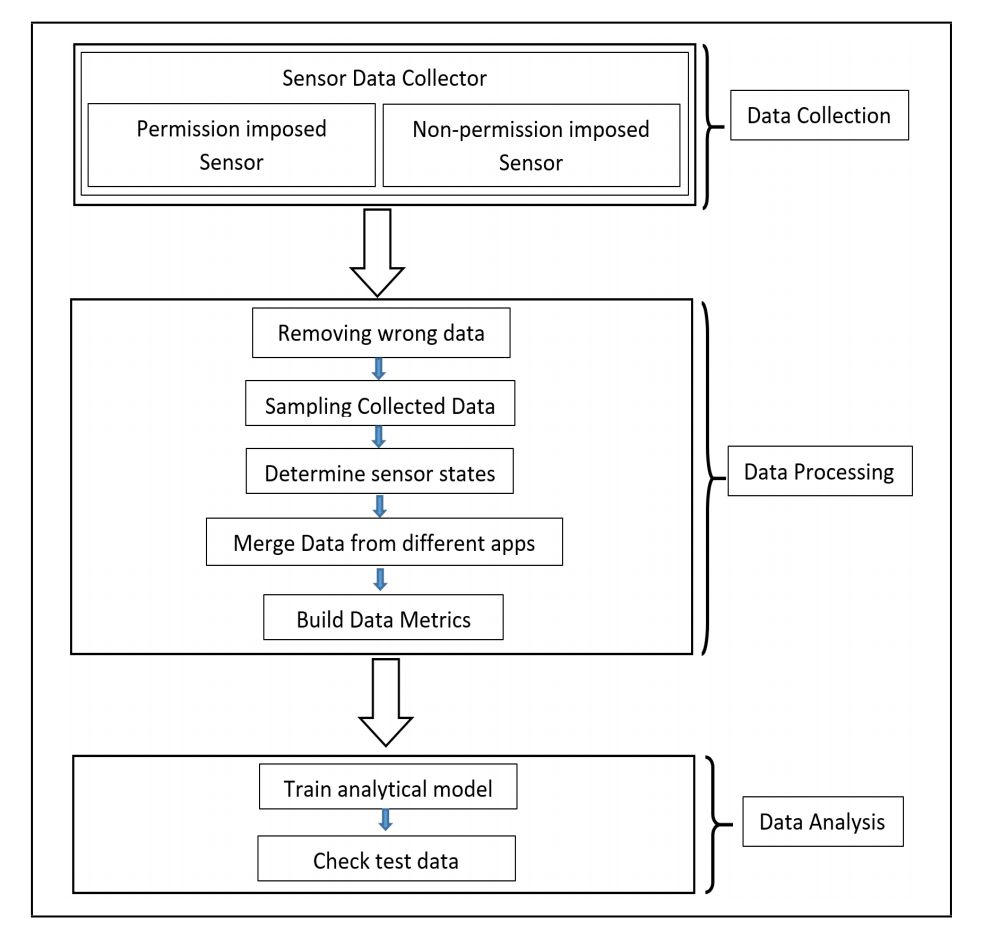
There are three phases in 6thSense – data collection, data processing, and data analysis.
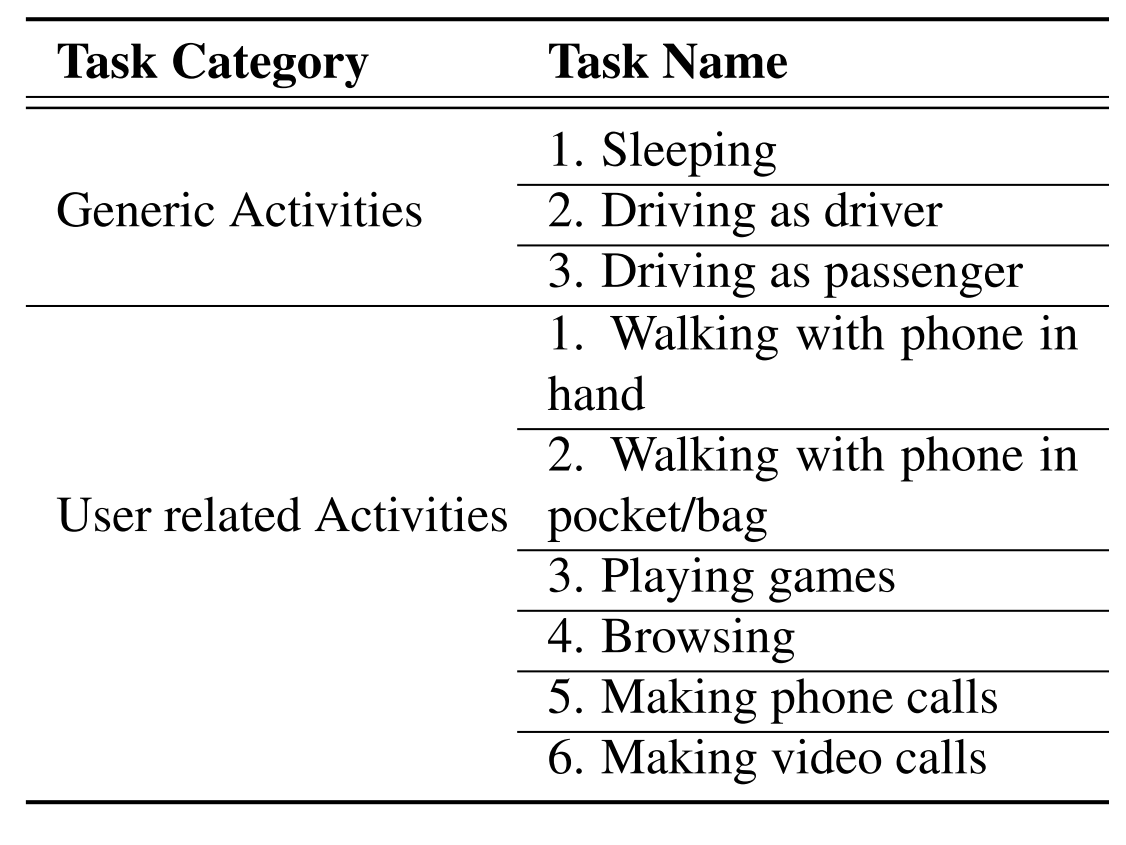
Data collection: In data collection phase, we collect data from different sensors over a certain period. We choose nine different sensors of smart devices which are enough to build a context-aware model of user activities. These are – accelerometer, gyroscope, light sensor, proximity sensor, GPS, audio sensor (microphone and speaker), camera, and headphone. We choose nine different user activity to collect the sensor data and build ground truth for proposed IDS framework. These user activities are given in the table.
Table: Typical Activities of Users on Smart Device
Data processing: After collecting sensor data for different user activity, we process the data to use these in the later phase. First, we remove missing data entries and clean the data. As different sensors have different frequencies, we have to sample the sensor data over a specific period. For 6thSense, we observe the change in the sensor condition in each second and from this per second change, 6thSense determines the activity of users. As our analytical model only take sensor condition (on/off) into account, we calculate the average of sensor data over one second and observe the change in sensor condition from the previous timestamp. If the sensor value is changing from the previous timestamp, we represent the sensor condition as 1 and 0 otherwise. These reorganized data then used in data analysis phase.
Data analysis: In data analysis phase, we use three different approaches (Markov Chain, Naïve Bayes, and Machine Learning Techniques) to analyze data from the previous phase. We use 75% of data for training purpose and rest of the data for testing purpose in 6thSense. Data used in training phase includes both benign and malicious activities. Test datasets are compared with the training model to distinguish malicious activities.
Figure: 6thSense Framework
Performance
We tested our framework against abovementioned threat model and conduct detail performance evaluation. Based on our test result, 6thSense achieves over 98% accuracy in all three detection approaches we adapted in this framework. Moreover, 6thSense introduces lower performance overhead (CPU and memory usage, battery usage, etc.) in smart devices.