Securing Sensory Side-Channels in Cyber-Physical Systems and IoT Devices and Applications 
Modern devices have become “smart” in recent years with the advancement of modern electronics and wireless communication systems. Smart devices such as smartphone, smartwatch, fitness trackers, etc. are equipped with high precision sensors, empowering them to gather information about user characteristics as well as the surrounding environment. These sensor-enriched devices have opened a new domain of sensing-enabled applications. With the rapid growth sensing-enabled applications, smart devices are integrated in every possible application domain, from home security to health care to military. Some applications can even learn characteristics of users using sensor data and take automatic decisions to improve the user experience.
Nevertheless, integration of different sensors in smart devices has introduced a novel way to exploit these devices. Using sensors an adversary can successfully attack a smart device by (1) triggering existing malware, (2) transferring malware, (3) leaking sensitive information, or (4) stealing valuable information. These sensor-based threats expose flaws in existing sensor management systems of smart devices. In this project, we investigate and develop a context-aware IDS, 6thSense, to address these sensor-based threats. Our proposed framework is built upon the observation that for any user activity or task in smart devices, a different, but a specific set of sensors becomes active. 6thSense monitor sensor data in real-time and learn how sensors’ states change with different activities. In training phase, we collect sensor data for different user activity and build a context-aware model of a task which is the ground truth of the framework. In the detection phase, 6thSense observes sensor data and checks against the ground truth. In 6thSense, three different approaches are used for detection method: Markov Chain, Naïve Bayes Model, and standard Machine Learning (ML) Techniques. Our proposed framework provides real-time sensor monitoring and shows higher accuracy in detecting sensor-based threats.
- Existing Sensor Management System
- Threat Model
- Assumptions and Features
- 6thSense Framework
- Performance
Existing Sensor Management System
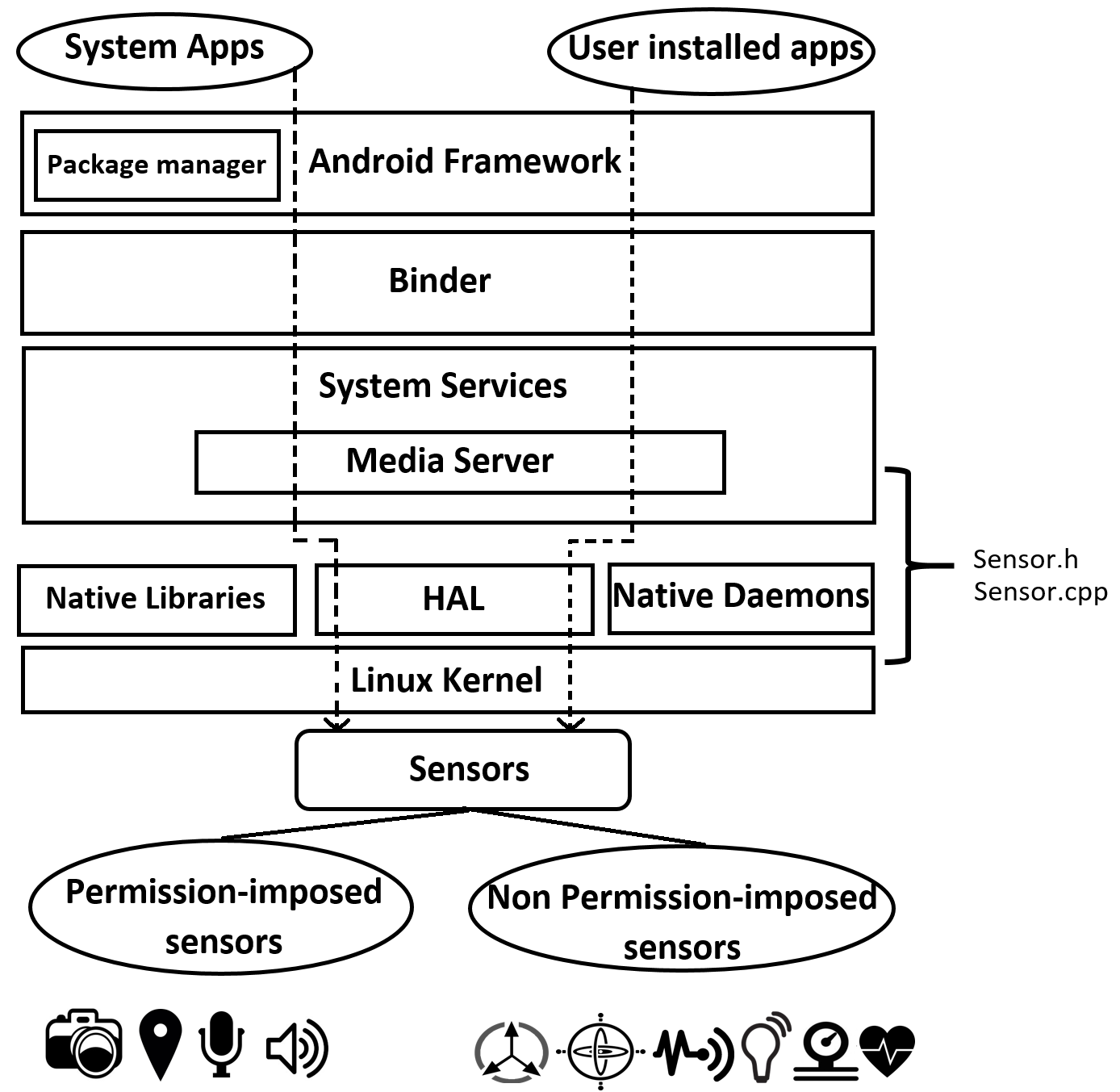
Present smart device operating systems (e.g., Android, Blackberry, iOS, Windows) do not provide any security measure to secure information flow between apps and sensors. Existing sensor management system is built upon permission-based access which is enforced only for selective sensors such as camera, microphone, GPS. Other sensors like gyroscope, light sensor, etc. are considered safe to access by any app. Lack of knowledge about sensor-based threats leads to overlook this design issue. Again, once a user accepts sensor access permission, he/she will have no information regarding how the app is using sensor data in the system. Hence, the existing sensor management system fails to provide complete security to on-board sensors of a smart device.
Figure: Android sensor management system
Threat Model
For testing 6thSense, we classify three different threat models.
Threat 1: Triggering a malicious app via sensor: A malicious app that is already been installed in the device can be triggered by sending a specific pattern via sensors.
Threat 2: Information leakage via sensor: A malicious app existed in the device can leak information (saved or gather in real time) to attackers via sensors.
Threat 3: Stealing information via sensor: A malicious app can exploit camera of a device and capture pictures stealthily when the device is in sleep mode.
Assumptions and Features
For designing 6thSense, we note following design assumptions and features:
Sensor co-dependence: Sensors in smart devices are usually considered as independent components. But for designing 6thSense, we assume that sensors are co-dependent entities. For each user activity on the smart device, a specific set of sensors remains active. For example, if a person is making a call, audio and proximity sensor will remain active. Hence, a co-dependent relation exists between sensors while executing a task. As each activity uses a specific but different set of active sensors to perform the activity, we can distinguish between normal user activity and malicious activities by observing active sensors. 6thSense uses the contexts of all sensors to build the IDS framework and detect malicious activities on the device.
Adaptive sensor sampling: Smart devices come with different sensors which have different ranges of frequencies. To observe and collect sensor data over a specific period, sensor data must be sampled according to sensor frequency correctly. If individual sensor frequency is considered, there may be missing data which will introduce error in the detection method. 6thSense address this issue and sample sensor data over a fixed time period instead of individual sensor frequency.
Faster computation: Smart devices are integrated with the high precision sensors which collect a huge volume of data over a short period for increasing accuracy. To process this data, a faster computation method should be used in proposed security measures. In 6thSense, we use Markov Chain, Naïve Bayes and Machine Learning techniques which are proven simple and faster computation techniques.
Real-time monitoring: A possible way of abusing the sensors is false data injection. If false data is injected, it will introduce error in IDS. To mitigate this issue, 6thSense provide real-time monitoring of sensor data on smart devices.
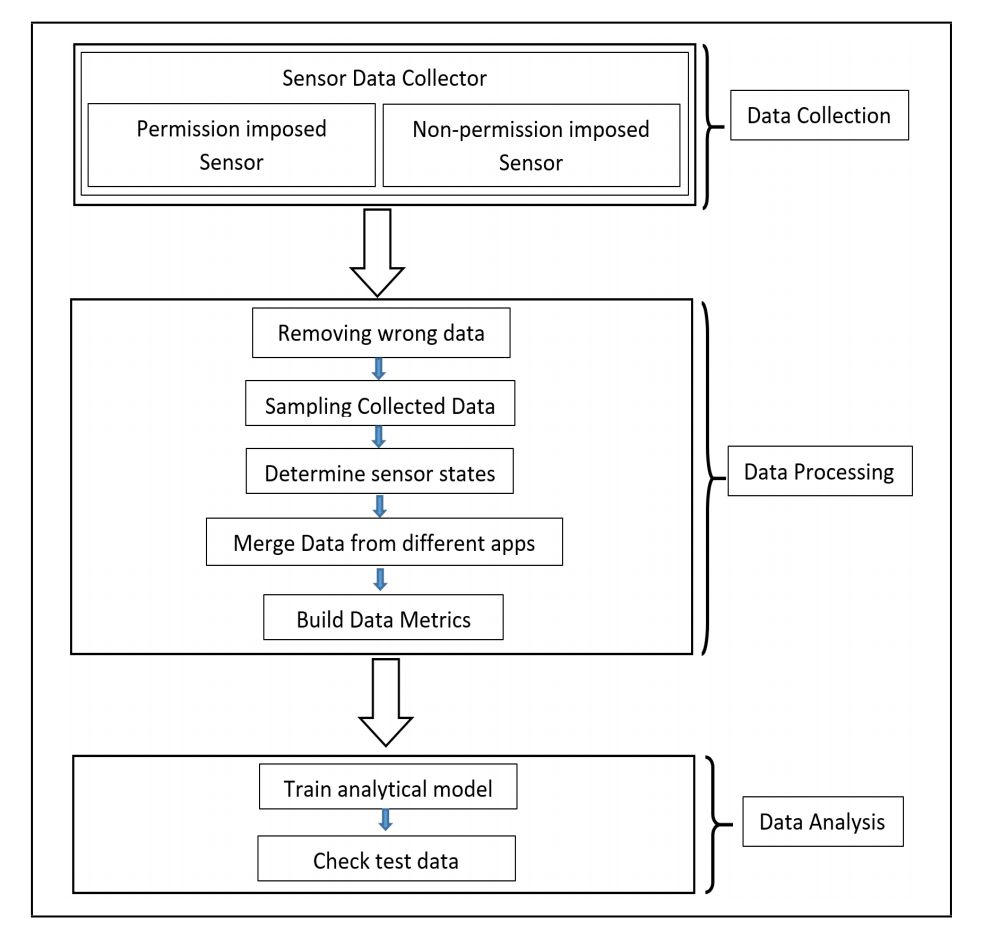
6thSense Framework
There are three phases in 6thSense – data collection, data processing, and data analysis.
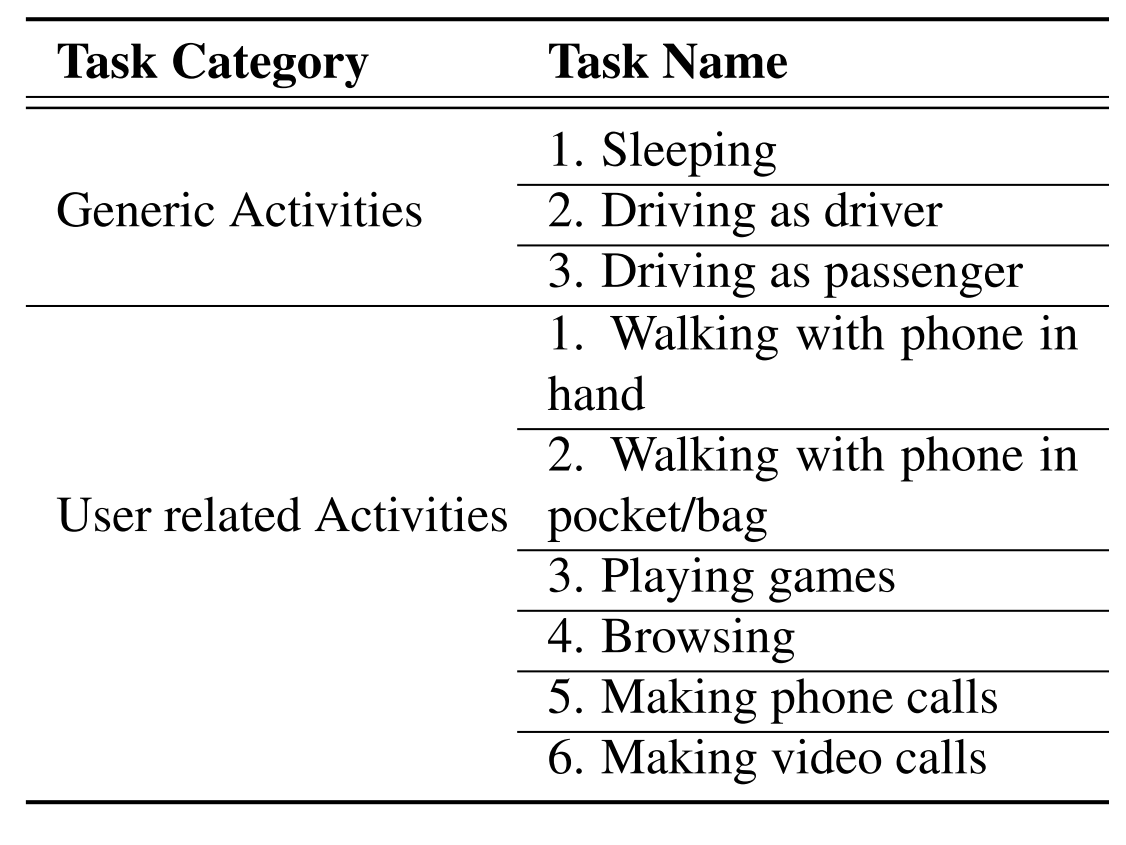
Data collection: In data collection phase, we collect data from different sensors over a certain period. We choose nine different sensors of smart devices which are enough to build a context-aware model of user activities. These are – accelerometer, gyroscope, light sensor, proximity sensor, GPS, audio sensor (microphone and speaker), camera, and headphone. We choose nine different user activity to collect the sensor data and build ground truth for proposed IDS framework. These user activities are given in the table.
Table: Typical Activities of Users on Smart Device
Data processing: After collecting sensor data for different user activity, we process the data to use these in the later phase. First, we remove missing data entries and clean the data. As different sensors have different frequencies, we have to sample the sensor data over a specific period. For 6thSense, we observe the change in the sensor condition in each second and from this per second change, 6thSense determines the activity of users. As our analytical model only take sensor condition (on/off) into account, we calculate the average of sensor data over one second and observe the change in sensor condition from the previous timestamp. If the sensor value is changing from the previous timestamp, we represent the sensor condition as 1 and 0 otherwise. These reorganized data then used in data analysis phase.
Data analysis: In data analysis phase, we use three different approaches (Markov Chain, Naïve Bayes, and Machine Learning Techniques) to analyze data from the previous phase. We use 75% of data for training purpose and rest of the data for testing purpose in 6thSense. Data used in training phase includes both benign and malicious activities. Test datasets are compared with the training model to distinguish malicious activities.
Figure: 6thSense Framework
Performance
We tested our framework against abovementioned threat model and conduct detail performance evaluation. Based on our test result, 6thSense achieves over 98% accuracy in all three detection approaches we adapted in this framework. Moreover, 6thSense introduces lower performance overhead (CPU and memory usage, battery usage, etc.) in smart devices.
Publications:
- K. Denney, A. S. Uluagac, K. Akkaya and S. Bhansali, “A novel storage covert channel on wearable devices using status bar notifications,” 2016 13th IEEE Annual Consumer Communications & Networking Conference (CCNC), Las Vegas, NV, 2016, pp. 845-848.
doi: 10.1109/CCNC.2016.7444898 - A. S. Uluagac, V. Subramanian and R. Beyah, “Sensory channel threats to Cyber Physical Systems: A wake-up call,” 2014 IEEE Conference on Communications and Network Security, San Francisco, CA, 2014, pp. 301-309.
doi: 10.1109/CNS.2014.6997498 - Amit Kumar Sikder, Hidayet Aksu, and A. Selcuk Uluagac, “6thSense: A Context-aware Sensor-based Attack Detector for Smart Devices”, In proceedings of 26th USENIX security symposium, Vancouver, Canada, 2017. [PDF], [BibTex]
- Amit Kumar Sikder, Hidayet Aksu, and A. Selcuk Uluagac, “A Context-aware Framework for Detecting Sensor-based Threats on Smart Devices”, IEEE Transactions on Mobile Computing (2019). [PDF], [BibTex]
- Amit Kumar Sikder, Leonardo Babun, Hidayet Aksu, and A. Selcuk Uluagac, “Aegis: A Context-aware Security Framework for Smart Home Systems”, Accepted to appear in 2019 Annual Computer Security Applications Conference (ACSAC), Puerto Rico. [PDF] [BibTex]
Invention Disclosures:
- Amit Kumar Sikder, Hidayet Aksu, and A. Selcuk Uluagac, “A context-aware Intrusion Detection method for smart devices with sensors”, submitted to Florida International University and accepted by United State Patent and Trademark Office (US 10,417,413 B2). [PDF] [BibTex]
Media Coverages:
- Guard Your Gadgets: Channel 7 covers our project in evening news on November 11, 2016.
- Dangers of Unsecured Surveillance Cameras: NBC 6 news highlights a news featuring unsecured surveillance cameras where Dr. A. Selcuk Uluagac talked about how camera sensors can be hacked in surveillance cameras.
- Your phone is like a spy in your pocket: Science News highlights our research work in their magazine on February, 2018. Magazine issue: Vol. 193, No. 2, February 3, 2018, p. 18.
Presentations and Talks:
- Amit Kumar Sikder, H. Aksu, and A. S. Uluagac, 6thSense: Sensor-based Attack Detector for Smart Devices, Technical Presentation at Graduate Student Appreciation Week (GSAW) in Florida International University, Miami, 2017.
- Amit Kumar Sikder, H. Aksu, and A. S. Uluagac, 6thSense: Sensor-based Attack Detector for Smart Devices, Technical Presentation at 26th USENIX security symposium, Vancouver, Canada, 2017.
- Amit Kumar Sikder, Abbas Acar, Leonardo Babun, and A. S. Uluagac, Experts talk cyber attacks on business, lead live ‘hack’, Workshop on cyber security leadership and strategy, hosted by Florida International University, the U.S Chamber of Commerce, the Florida Small Business Development Center Network and the Greater Miami Chamber of Commerce.
** Project Name: CAREER: Securing Sensory Side-Channels in Cyber-Physical Systems
Project Sponsor: National Science Foundation
Project Duration: 06/01/15-05/31/20
Award Number: 1453647.