Project Overview 
Our everyday lives are expanding fast with the introduction of new Smart Home Systems (SHSs). Today, a myriad of SHS devices and applications are widely available to users and have already started to re-define our modern lives. Smart home users utilize the apps to control and automate such devices. Users can develop their own apps or easily download and install them from vendor-specific app markets. App-based SHSs offer many tangible benefits to our lives, but also unfold diverse security risks. Several attacks have already been reported for SHSs. However, current security solutions consider smart home devices and apps individually to detect malicious actions rather than the context of the SHS as a whole. The existing mechanisms cannot capture user activities and sensor-device-user interactions in a holistic fashion. To address these issues, in this project, we introduce Aegis, a novel context-aware security framework to detect malicious behavior in a SHS. Specifically, Aegis observes the states of the connected smart home entities (sensors and devices) for different user activities and usage patterns in a SHS and builds a contextual model to differentiate between malicious and benign behavior. We evaluated the efficacy and performance of Aegis in multiple smart home settings (i.e., single bedroom, double bedroom, duplex) with real-life users performing day-to-day activities and real SHS devices. We also measured the performance of Aegis against five different malicious behaviors. Our detailed evaluation shows that Aegis can detect malicious behavior in SHS with high accuracy (over 95%) and secure the SHS regardless of the smart home layout, device configuration, installed apps, and enforced user policies. Finally, Aegis achieves minimum overhead in detecting malicious behavior in SHS, ensuring easy deployability in real-life smart environments.
Project Description
- Smart Home System (SHS)
- Threat Model
- Design Features Considered by Aegis
- Aegis Framework
- Performance
Smart Home System
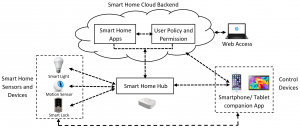
In following figure, a typical architecture of a SHS is shown. A SHS has four basic building blocks as shown in Figure 1. The first block of the SHS comprises sensors and devices in the system. These smart home devices and sensors are connected to each other via a smart hub. As there is no generic interoperability standard among smart home devices, the hub provides a common access point for all the entities in the SHS. The hub is connected to both cloud backend service and smartphone/tablet companion app. Users can use the smartphone app to control the smart home entities or install different apps from the app stores. Indeed, we can group SHS architectures in two main categories: a cloud-based architecture where the installed apps run in the cloud backend (e.g., SmartThings), and hub-based architecture where the installed apps run the hub locally (e.g., Apple HomeKit).
Figure: A smart home environment and its major components
Threat Model
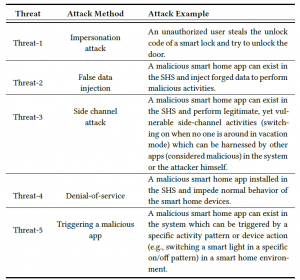
For testing Aegis, we classify five different threat models.
Design Features Considered by Aegis
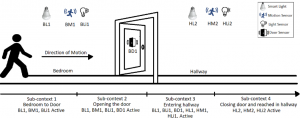
Context-awareness: Context-awareness refers to the ability of a system to use situational and environmental information about the user, location, and devices to adapt its operation accordingly. In a SHS, all the sensors and devices follow different trigger-action scenarios to perform tasks. Here, sensors are used to provide input in the devices (trigger) and devices take autonomous decisions (actions) based on these inputs. When a user performs a task in a SHS, several smart home sensors and devices may become active in a sequential pattern. The pattern of active devices and sensors is different but specific for distinct user activities. Existing SHS cannot observe these patterns in sensors’ and devices’ states over time and can not understand the context of the user activity. For example, while a user moves from one bedroom to a hallway, several devices and sensors become active in a sequential manner (Figure~\ref{context}): moving towards bedroom door (sub-context 1: BL1, BLi1, BM1 are active), bedroom door opens (sub-context 2: BL1, BLi1, BM1, BD1 are active), entering the hallway (sub-context 3: BL1, BLi1, BD1, HLi2, HL2, HM2 are active), bedroom door and light close and reaches the hallway (sub-context 4: HLi2, HL2, HM2 are active). To complete the activity (moving from the bedroom to the hallway), the user must follow the sub-contexts in the same sequential pattern. The user cannot skip one specific sub-context and move to the next one to complete the activity. For instance, the transition from sub-context 1 to sub-context 4 is not possible as a user cannot go to the hallway from the bedroom without opening the door. Motivated by this, Aegis is designed to understand this property of SHS to build a context-aware model for different user activities and usage patterns and differentiates between benign and malicious activities of smart home devices and sensors.
Sensor-device co-dependence: In a SHS, sensors, and devices can be configured as independent entities. However, they work in a co-dependent manner to provide autonomous functionalities. For instance, smart lights can be configured with motion sensors to light up when motion is sensed. Here, the smart light depends on the input from the motion sensor while the motion sensor alone cannot provide any significant function in a SHS. The functions of devices and sensors create a co-dependent relationship with each other. In this way, sensors and devices in the SHS can build many-to-many co-dependent relationships. However, existing SHSs do not consider this co-dependent relationship and can not visualize the context of a user activity by observing the usage pattern of smart home entities. In short, sensors and devices in a SHS are configured as independent components, but in reality, they are function-wise co-dependent. Aegis considers these relations to build the context of the user activities in a SHS.
User activity-device correlation: In a SHS, different users utilize and control smart home devices in multiple ways. For instance, a user can set a security camera to take pictures whenever a motion is detected in the associated motion sensors. On the other hand, users control devices in multiple ways. For example, a user can unlock a door by using the smartphone app or entering the code manually. Here, the state of the lock can be determined by user activity on the smartphone or by using a presence sensor to detect the user near the smart lock. In short, by observing the user activities in a SHS, it is possible to determine the normal operation of smart home devices. One can define normal or malicious user behavior with the user activity-device correlation. Current SHS cannot correlate user activity and device actions correctly, which is considered as a feature in Aegis to differentiate benign and malicious activities.
Aegis Framework
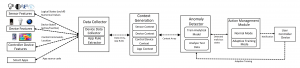
Aegis has four main modules: (1) data collector, (2) context generator, (3) data analysis, and (4) action management. First, Aegis collects data from smart home entities (sensors and devices) for day-to-day user activities. The data collector module uses an app to collect all the device states (active/inactive) from the hub. Additionally, this module collects rules generated by different smart apps using the app rule extractor.
The device state data is used to understand the context of the user activities and feeds the context generation module. This module creates context arrays depending on usage patterns and the predetermined user policies in the smart apps. Each context array contains overall information of the user activities and device states in the SHS.
The context arrays generated in the context generation module are used by the anomaly detector module to implement machine learning-based analysis and build the context-aware model of the SHS. Additionally, anomaly detector module decides whether or not malicious activities occur in the SHS.
Finally, the malicious activities detected by the anomaly detector module are forwarded to the action management module. This module notifies the users regarding the unauthorized activities. Also, it offers adaptive training mode where users can validate any false positive or false negative occurrence and re-train the detection model to improve the performance of Aegis.
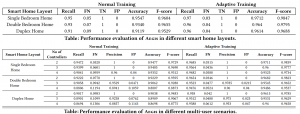
Performance
We tested Aegis in real smart home systems where 15 different users performed typical daily activities in three different home layouts generating over 55000 sensor-device correlated events. Furthermore, we considered different device settings (sensor-device relations), apps, and user policies to evaluate the performance of Aegis against five different threats. Our extensive evaluation demonstrates that Aegis can detect different threats to smart home system with high accuracy and F-score (over 95%). In addition, Aegis achieves minimum overhead in terms of latency and resource usage making Aegis compatible for real-life deployment.
Publications:
- Amit Kumar Sikder, Leonardo Babun, Hidayet Aksu, and A. Selcuk Uluagac, “Aegis: A Context-aware Security Framework for Smart Home Systems” In proceedings of 35th Annual Computer Security Applications Conference (ACSAC), San Juan, Puerto Rico. 2019.
Invention Disclosures:
- Amit Kumar Sikder, Hidayet Aksu, and A. Selcuk Uluagac, “A context-aware intrusion detection method for a smart home, office, and building systems with smart devices”, submitted to Florida International University.